Security incidents related to customer data have risen dramatically. Using data from the
ITRC 2020 Data Breach Report,
Statista.com found that “in 2020, the number of data breaches in the United States came in at a total of 1,001 cases. Over the course of the same year, over 155.8 million individuals were affected by data exposures...due to less-than-adequate information security.” The total economic impact of these breaches reaches into the billions of dollars, with the average breach costing $7.9 million.
Organizations have a lot riding on security. So,
what do content and metadata have to do with it? There are hidden killers lurking in the content infrastructure of most organizations. If left unnoticed and unchecked, they are capable of inflicting enormous pain on an organization and its customers.
The Three Hidden Killers of Information Security
The least-noticed contributors to security breakdowns can be found in three important places:
- The policy an organization maintains around content and data.
- The governance and operations structure around content.
- The metadata profile stored along with content items.
If neglected, these hidden killers can leave open enormous vulnerability gaps and systemic issues that can cripple overall information security. But, if intentionally resourced and managed, these ‘killers’ can actually become contributors to security
Modular Content, Modular Security
Content and data assets, even at the modular level, can and should store an understanding of what they are, where they come from, and who should consume them.
Security and permissions can be built in at the level of individual modules. Permission-based content targeting requires clear content access rights to be made available at the level of the content module. Security must tie into the content structures—specifically the metadata—of the content sets.
Without functioning policy, operations, and controlled metadata information, security risk spreads across information sets. Breaches can then end up exposing untethered, non-policy-managed content and data assets to nefarious actors.
While data breaches have many causes, information security should consider the defensive hardness of the content assets themselves. Content leaders have a responsibility to ensure security from the assets on up
The Cost of Unstructured Boundaries
Too often, a company’s policies and procedures have grown into thick “how-to” instructions, originally in 3-ring shelfware–now evolved into fat PDF files, that are rarely remembered or consulted. This has partly stemmed from content governance being treated as a series of unpleasant, rigid rules. Content creators may think they prefer a world with no rules in which they exercise unlimited creativity against a blank canvas. Alas, that free-spirited approach always comes with a cost.
In today’s world of
omnichannel content, drawn from many disparate sources (including partners and contractors), it's simply dangerous to ignore structures. As the systems and tools to create and collaborate increase our capabilities and sophistication, the need for safety guidelines and policies also increases. But policies are not enough; they have to live and breathe in the
content models, the infrastructure and tools, and in the day-to-day operations practice surrounding content.
Too often, organizations opt to ignore and absorb the risk and cost of continuing ‘how we’ve always done it’. Unknowingly, the lack of governance leads to increases in:
 Regulatory risk and exposure
Regulatory risk and exposure - Team frustration and lack of motivation
- Unclear responsibilities and processes
- Regulatory compliance negligence and fines
- Brand dilution
- Duplication of effort
- Lack of reuse
- Inconsistencies in quality
Rather than hemorrhaging these issues,
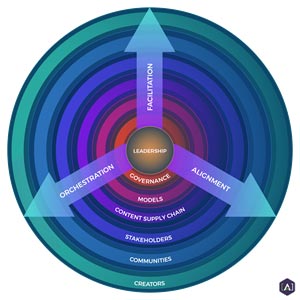
content leaders are waking up to the benefits of a unified governance and operations approach. Within Content Operations engagements, [A] works with clients to design and implement a Content Orchestration Model (COM), that is engineered to enhance existing technology architectures, facilitates content creation efficiency, and provides policy adherence. Governance is not an afterthought; compliance is purposely designed early within the content supply chain so that creators can flourish within a pre-defined and constructed boundary.
Playing within Safe Boundaries
In [A]’s
Towards a Smarter World podcast series, guest
Kristina Podnar made some encouraging
observations about end-user benefits with governance integrated into the content supply chain.
“You tell your kids they can go play, they can do whatever they want to. They just can’t leave the confines of your backyard and that fence. It’s there to keep them safe. Now, they can do lots of crazy things. They can take the broom that’s out there or the rake and they can pretend it’s a horse. They can race worms like my child used to do. They can throw sand up in the air and pretend it’s snowing.”
“But the reality is that they’re safe in that backyard. We know they’re not going to get run over by a car. We know nothing bad is going to happen to them. And when they’re ready for dinner, they can come inside. And it’s the same thing with policies. When you actually create policies, what you create for the organization, the enterprise for content creators or anybody else who is involved in digital is a nice, safe place where they can be creative, they can be innovative.”
You can find even more insights in Podnar’s book,
The Power of Digital Policy.
Build In Policy and Security into Content Models
A key part of the security foundation can be built by
implementing more thoughtful metadata procedures. We need to expand our
content models with function-oriented elements that contain properties such as:
- Ownership
- Expiration
- Policies
- Regulations
- Read and Write Permissions
- Accessibility Variance
- Geographic Regulations
- Privacy Policy Variables
These content model elements, or metadata fields, provide the tremendous power of discrete controls and capacities to the content assets within a managed content supply chain. Rather than allowing the chaos of each department maintaining disparate metadata with no policy adherence, a Core Content Model is able to unify and encompass a complete and shared metadata profile.
An added benefit of
using [A]'s Core Content Model approach, is the ability to control and define mappings of content elements across channels and systems—the ability to perform nodal transformations.
Centralized Orchestration for Downstream Adherence and Efficiency
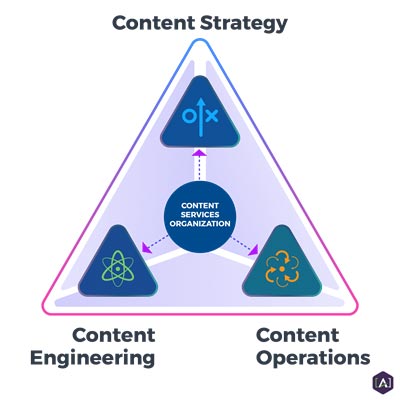
The most efficient content supply chains are run by a centralized, cross-functional
Content Services Organization (CSO). This organization is composed of three separate practices:
Content Strategy,
Content Engineering, and
Content Operations.
To learn more about the CSO, see the referenced
2019 TechComm journal article or
simplea.com for our additional resources. This can be coached and internally trained or driven by an integrated partner. In any form, it is needed.
Ensuring an optimized content supply chain for efficiency and compliance starts with a COM. It ties together policy considerations, business and publishing processes, defined content models, and stakeholder needs into a cleanly defined and “living” specification. It takes real orchestration, and that requires discovery and strategy before it happens. A Content Services Organization has dedicated staff to make sure that all aspects of content coordination work smoothly and are scalable.
5 Common Questions About Security
1. How do we build content sets that are consistently aligned with an organization’s regulatory and security mandates?
By baking security guidelines into the solution using policy, operations, and metadata, we can ensure consistency across company mandates.
2. Who oversees and supports the security-aligned processes and procedures for creating content?
Processes are facilitated by a dedicated Content Operations function that references a written Content Orchestration Model, incorporating security standards.
3. How do we automate security considerations into workflows?
Automation can be achieved by designing a content supply chain, enhanced by the security policies threaded into content sets using the disciplines and practices of content engineering.
4. Where in the organization do policyaligned and compliant content practices get defined?
Within an organizational-wide Content Services Organization (CSO) that oversees and addresses these issues, among others.
5. How do we maintain security measures across all channels and platforms?
By expanding content models with permission metadata within content elements that are mapped to, and able to transform for use, across systems and channels.
Information Security Starts at Home
The pain resulting from a lack of regulation and security can be very heavy. We’ve seen organizations in various industries struggle with finding material and wasting anywhere from 20-60 percent of their time manually transforming content from place to place or system to system. Not only is this costly in overhead, but these manual processes allow for more security risks to seep into procedures. But all of that risk is avoidable with planning.
Start with workshops that get the players into a common conversation. [A] hosts these, or they can be done internally. Yes, it does cost some money and time, but it is a lot less expensive to do things right up front than clean up after legal, regulatory, or security issues have gone wrong. It all starts with internal conversations, and then agreeing to get the house in order and secure. With customer confidence and billions of dollars in direct and indirect costs on the line, the industry will benefit by revisiting and expanding the pivotal role of policy and its connection to engineering and operations across content teams.
For more resources
Listen to our
"Digital Policy: Powering Operations, Innovation, and Velocity.” Towards a Smarter World podcast with Kristina Podnar and read our in-depth whitepapers introducing the
Core Content Model and the
Core Semantic Model.
Contact Us for a Free Consultation.